- A Buying Guide to Unified Threat Management Appliances
If you’ve done your research on unified threat management appliances and think they’re the way to go for you, then you’re most likely looking into the next steps of your security venture, and how you can choose the best appliance for you and your needs.
We’ve also done some research, and we’ve put together a guide for helping you buy the ideal unified threat management appliance to suit you and to ensure your data is safe online.
Identify the specific security functionality that you require
 It sounds pretty obvious but many people do tend to skip this step and go shopping for their appliance without actually identifying what it is they’ll need it to do specifically. This is a mistake that could end up costing you more than you’d need to pay, so take some assessment time before you start looking.
It sounds pretty obvious but many people do tend to skip this step and go shopping for their appliance without actually identifying what it is they’ll need it to do specifically. This is a mistake that could end up costing you more than you’d need to pay, so take some assessment time before you start looking.
Look into pricing and flexibility
It is really important to establish whether you will have to pay for functionality; such as email security even if you don’t actually need it, or whether you can just select the security features you need. Don’t forget to look at the ongoing subscription costs (for anti-virus signature updates, URL blacklists, support, and so on) as well as the upfront cost. Look into reputable companies like Threat Management – Dell.
Research how easy they are to set up and maintain
If you’re required to set up the device yourself, you’ll need to determine how easy it is to do so, because if you haven’t got any experience with this sort of thing, it can be pretty easy to make a mistake. Likewise, you’ll want to evaluate what should happen if anything was to go wrong with along the way; i.e. will you have a guarantee and ongoing support, and will automatic updates be included, etc.
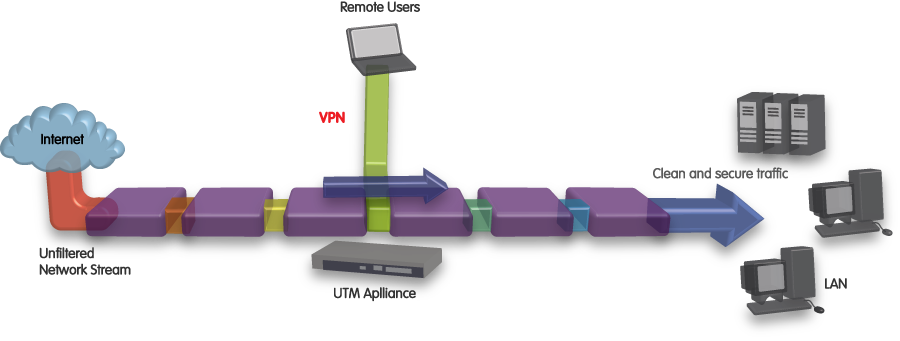
Determine whether you’ll need it to be able to cover remote workers
If you have people working for or with you that aren’t always working from the office, it’s a good idea to look into options that will help these workers to be covered for security issuestoo. Unless you plan on deploying unified threat managements appliances at a number of locations, you’ll need to link your branch offices to your main unified threat management appliance.
Look into their secure wireless capabilities
If you have a wireless LAN (more info on that here) in your work environment, you’ll need to look into ways in which a unified threat management system will work with it to keep your data safe. Some unified threat management systems deliver secure wireless connectivity, enabling you to offer wireless users, including guests, the same security controls as wired LAN users.





